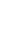Security Subsystem
A security subsystem in a System on Chip (SoC) is a dedicated hardware and software component that ensures the security of the system against various cyber threats. The security subsystem includes a range of security features, such as authentication, encryption, access control, and secure boot.
The security subsystem in an SoC typically includes a secure processor or a secure co-processor, which is responsible for executing the security functions. The secure processor is isolated from the main processor and has its own memory, which is used to store sensitive data and cryptographic keys. The secure processor is designed to be tamper-proof and resistant to attacks, such as side-channel attacks and reverse engineering.
The security subsystem also includes hardware-based security mechanisms, such as secure boot, which ensures that only authorized firmware and software are loaded and executed on the SoC. The secure boot process includes cryptographic verification of the firmware and software images and ensures that they have not been tampered with or modified.
Another important component of the security subsystem is the cryptographic engine, which provides hardware acceleration for various cryptographic functions, such as encryption, decryption, key generation, and hashing. The cryptographic engine is designed to be fast and efficient, and it is often optimized for specific cryptographic algorithms, such as AES or RSA.
In addition to the hardware components, the security subsystem also includes software components, such as secure boot loaders, secure firmware, and secure operating systems. These software components are designed to work seamlessly with the hardware components and provide a complete end-to-end security solution for the SoC.
Overall, the security subsystem in an SoC is a critical component that ensures the security and integrity of the system. It provides hardware-based security mechanisms that are resistant to attacks and ensures that only authorized firmware and software are loaded and executed on the SoC.
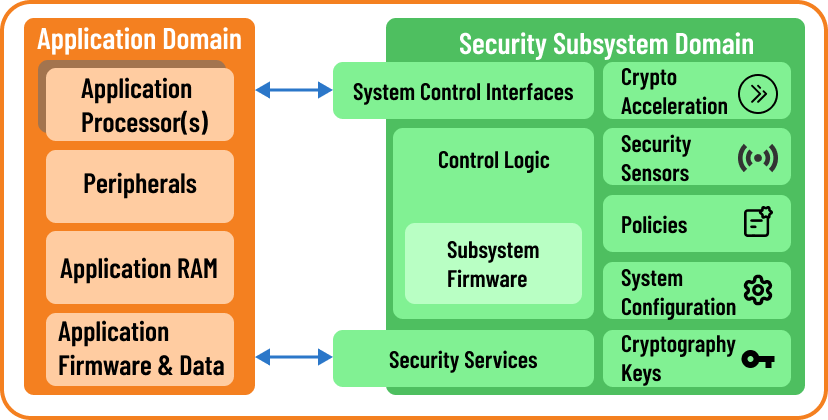
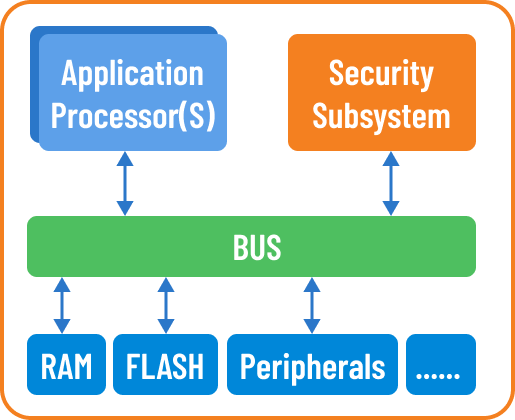
- A security subsystem is a dedicated subsystem within SoC Several terms refers to such subsystem, including integrated security subsystems. In the automotive market, they are often referenced as the secure hardware extension (SHE) module or the hardware security module (HSM).
- A security subsystem in a System on Chip (SoC) is a dedicated hardware and software component that ensures the security of the system against various cyber threats. The security subsystem includes a range of security features, such as authentication, encryption, access control, and secure boot.
- The security subsystem in an SoC typically includes a secure processor or a secure co-processor, which is responsible for executing the security functions. The secure processor is isolated from the main processor and has its own memory, which is used to store sensitive data and cryptographic keys. The secure processor is designed to be tamper-proof and resistant to attacks, such as side-channel attacks and reverse engineering.
- The security subsystem also includes hardware-based security mechanisms, such as secure boot, which ensures that only authorized firmware and software are loaded and executed on the SoC. The secure boot process includes cryptographic verification of the firmware and software images and ensures that they have not been tampered with or modified.
- Another important component of the security subsystem is the cryptographic engine, which provides hardware acceleration for various cryptographic functions, such as encryption, decryption, key generation, and hashing. The cryptographic engine is designed to be fast and efficient, and it is often optimized for specific cryptographic algorithms, such as AES or RSA.
- The security subsystem is embedded into SoC and equipped with controls and provided access to system resources. During the power-on, security system is one of the first entities to be initialized.
- Primary objective of security subsystems are providing security services to the application, provide platform security and protect platform integrity, and protect cryptographic keys from software attacks.
- Overall, the security subsystem in an SoC is a critical component that ensures the security and integrity of the system. It provides hardware-based security mechanisms that are resistant to attacks and ensures that only authorized firmware and software are loaded and executed on the SoC
Support Activities
Verify subsystem connectivity and basic function
Synthesize all RTL
Create subsystem testbench with standard VIPs or new ones as needed
DFT insertion (scan/lbist, MBIST & ijtag)
Check performance of major interfaces
Place and Route RTL blocks and 3rd party hard macros
Floorplan each subsystem per top level plan
Iterate as necessary for timing closure
Create clock and placement constraints as necessary
Perform RTL/gate equivalence checks
Perform all LVS and DRC
Perform ECOs for SOC timing and floorplan closure and IP